INSIGHTCONNECT
Go Easier on Your Analysts with Automation
- Orchestrate
Connect processes across your IT and security teams with clear communication, collaboration, and integration. - Automate
Streamline your manual, repetitive tasks with connect-and-go workflows – no code necessary. - Accelerate
Supercharge your security operations with automation that drives efficiency – without sacrificing analyst control.
Realize tangible ROI
Return benefits to your organization that includes predictable outcomes as well as significant time savings.
Leverage existing systems
Integrate with your existing IT and security systems to establish workflows that address your cyber risks faster.
Script less, automate more
Eliminate the need to write python automation scripts while still freeing up your team to get their jobs done.

How Does It Work?
Streamline and accelerate highly manual, time-intensive, processes 24 hours a day. With more than 300 plugins to connect your IT and security systems — and a library of customizable workflows — you’ll free up your security team to tackle bigger challenges, while still leveraging their expertise.
Here's how you'll do it:
- Automate Incident Response
- Integrate IT and Security Systems
- Accelerate Vulnerability Management
- Simplify Human Decisioning
Get More Done With InsightConnect
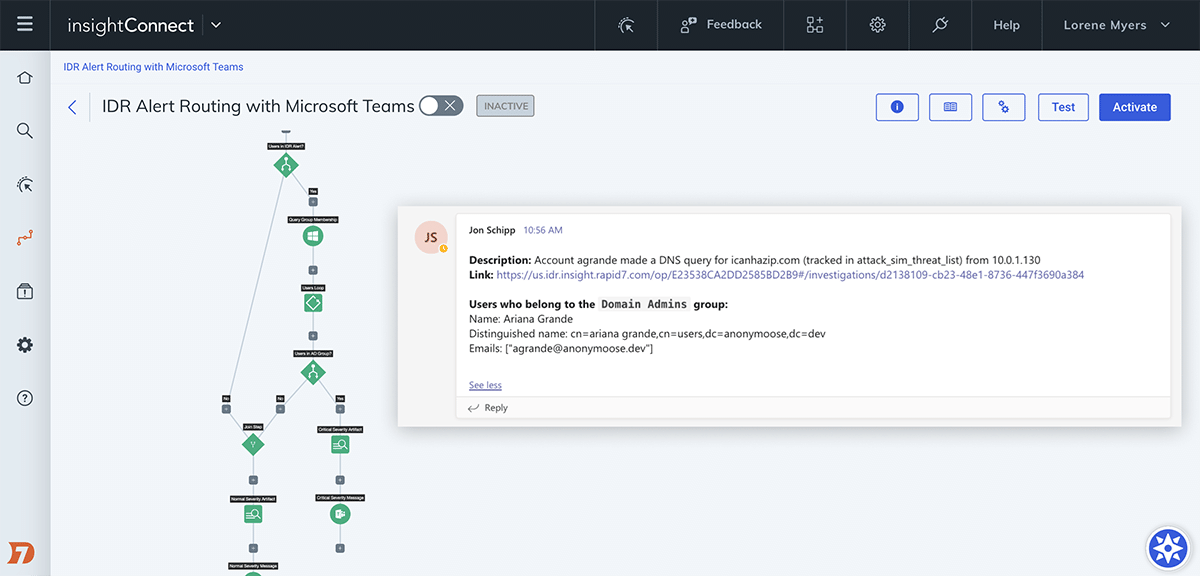
Accelerate Incident Response
Incident response can be time consuming. If you’re suffering from alert fatigue, you understand. New exploits are happening constantly. This makes keeping up a major challenge. Automate responses to the detection of suspect emails, user behaviors, attacker activity, and more. This frees your team to tackle more challenging security issues.
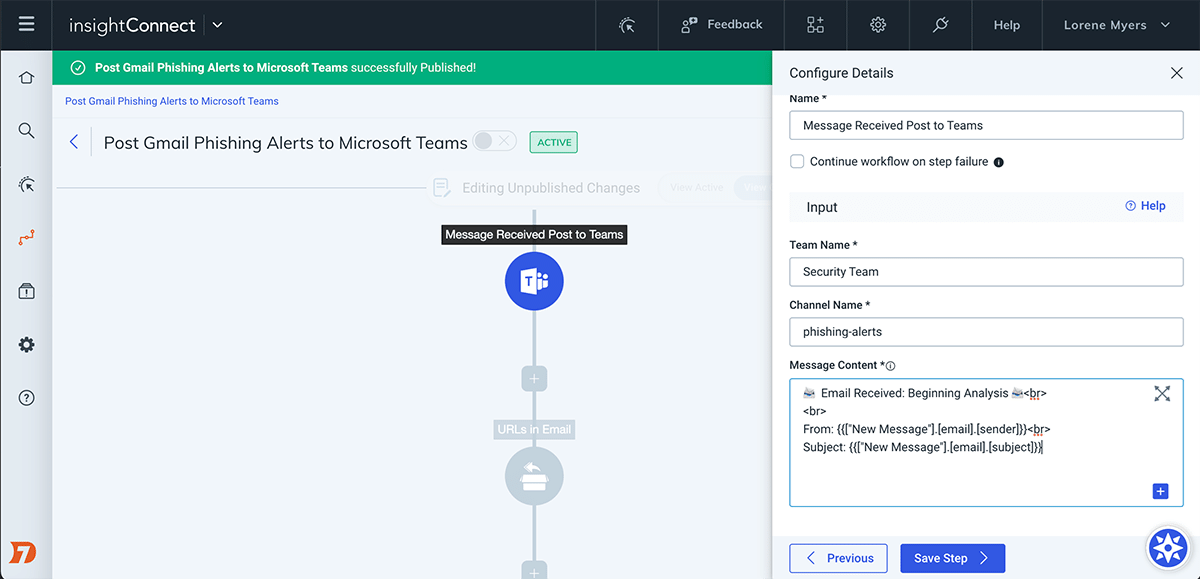
Learn MoreAutomate Phishing Investigations and Responses
Phishing remains the top attack vector behind most successful breaches. With InsightConnect, you'll move beyond manually investigating every suspect email, attachment, or URL as well as away from hand-deleting malicious emails and blocking phishers. Automate these repetitive, manual tasks so you can focus on more impactful strategies to stop malicious emails from landing in your organization.
Learn MoreVulnerability Management Automation
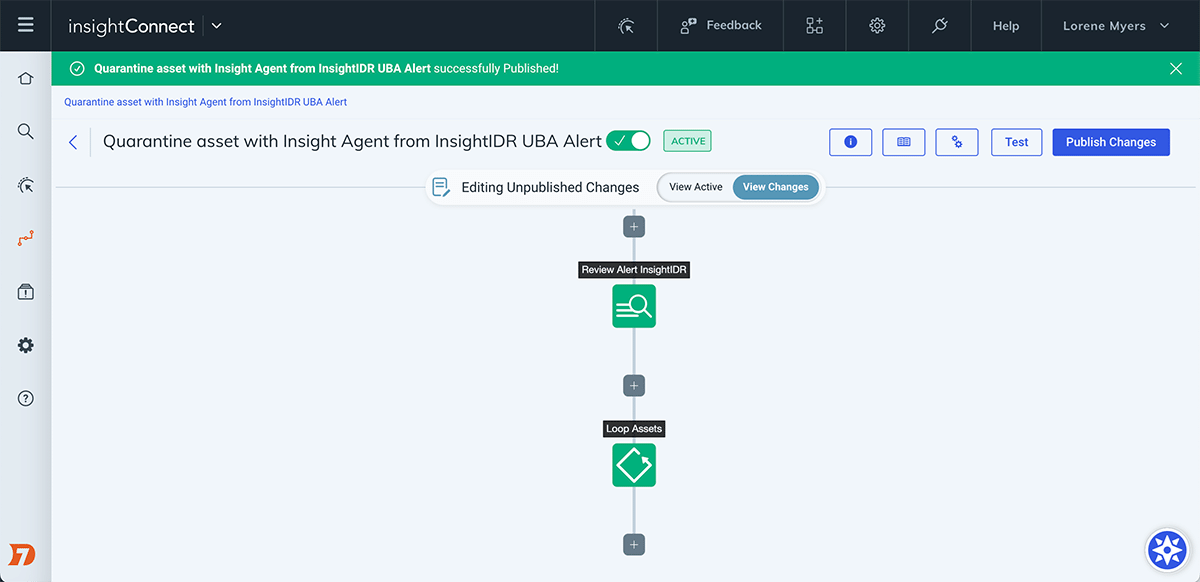
InsightConnect integrates with your existing IT and security systems to automate vulnerability management processes from notification to remediation, so you can ensure critical vulnerabilities are being patched. As part of addressing vulnerabilities, InsightConnect’s workflows enable cross-functional collaboration and human decisioning where needed. Automate steps like critical vulnerability alerting, patch discovery, remediation, verification, and more.
Learn MoreCollaborate With Ease
Leverage ChatOps systems like Slack or Microsoft Teams to increase visibility and coordinate incident response and vulnerability management processes. From these common communication tools, trigger workflows to automatically create new IT service tickets, kick off investigation and enrichment tasks, query users, and much more. InsightConnect integrates with ITSM solutions like ServiceNow and JIRA to ensure collaboration with IT, development, and other teams.
Learn MoreInvestigate and Contain Malware
With the growing prevalence of ransomware, cryptominers, RATs, and many other forms of malware, security teams need to investigate and quickly respond before minor outbreaks become major. With InsightConnect, you can automatically investigate and contain malware before it spreads and does significant damage to your organization.
Learn More